What Are Zero-Day Attacks?

A zero-day attack is a vulnerability or flaw that is unknown to the creators of a program or software.
When hackers exploit these vulnerabilities, they are already one step ahead, as the fact that a breach exists is simply not detected by the other side.
Such risks are extremely dangerous because they are one-sided, known by the attacker only.
Exploits can go unnoticed for years and are often sold for large amounts of money on the black market. The name “zero-day” stems from the day a software developer realizes there is a problem, which indicates the complexity of this threat.
How They Work
Unintended vulnerabilities found in software or operating systems are a major issue in the field of cybersecurity.
Incorrect device or security settings, as well as programming errors, can lead to such vulnerabilities and when left unaddressed, these security flaws can be exploited by cybercriminals.
In order to exploit a certain security weakness, hackers write specifically targeted code.
They store it in malware known as a zero-day exploit.
The malicious program exploits a weakness to impair the device or force unwanted actions.
This can normally be remedied by a patch from the software developer but until that point, there is not much protection that’s possible, making prevention the best policy.
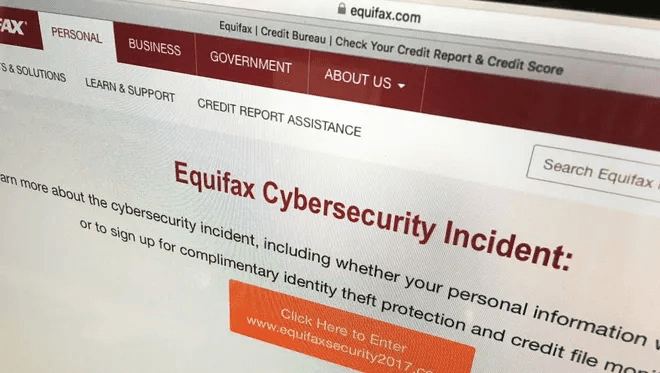
A well-known zero-day example of this type of threat is when the credit reporting agency Equifax was breached by hackers using an exploit on the Apache Struts web framework in 2017.
The vulnerability was said to have been fixed, but Equifax wasn’t able to actually patch it, and the hackers exploited that gap.
The Timeline Of A Vulnerability
This attack happens after a bug is exploited and attackers release malware before a developer can build a patch to repair the vulnerability.
If this vulnerability isn’t fixed, hackers will keep exploiting it.
Here’s a step-by-step timeline of what happens during this type of attack:
- Developers or vendors roll out new software in the market, but they are unaware of a possible vulnerability in their product.
- Hackers and other malicious elements spot a vulnerability before the developer or the vendor gets to know about it, or before they can work on creating a patch/fix for said vulnerability.
- A hacker writes specifically targeted codes. This is then implemented to exploit the undetected vulnerability while it is still open and available.
- Once this code is released, sooner or later someone recognizes it. In some cases, the developer or the vendor notices it through rigorous testing and builds a patch to prevent further attacks.
How To Protect Yourself?
These attacks pose significant safety risks, causing your device and your personal data to be exposed to dangerous elements.
It’s clever to take proactive and reactive security measures to keep your computer and data secure.
Here are necessary steps that you can take to protect your device and data from these types of threats:
- Your primary wall of defense should be a robust antivirus software that protects your devices from both known and unknown threats. Note that traditional AVs relying on signature-based detection aren’t effective against these threats. Hence, you must choose a Next Generation Antivirus (NGAV) that offers heuristic and behavior-based detection. If you’re using a Windows PC, it’s a good idea to turn on the Windows Defender Exploit Guard as it has several useful features to protect you against zero-day attacks.
- The next thing you must do is to be proactive and install software patches and updates as soon as they’re released. This isn’t a comprehensive solution on its own, but it’ll definitely help reduce the risk of open threats.
- Make sure to follow safe browsing habits. Do not click on spam links, shady attachments, or download files from unverified websites. Most malware is transferred online, hence it’s important to be extremely cautious about the sites you visit and the downloads you choose.
- Configure your device and network security settings. Keep a backup of your files and folders, preferably on external devices, and use features like a password manager, file shredder, and other add-ons available with security suites.
Bottom Line
Awareness is vital when it comes to protecting yourself from unknown threats.
However, the nature of zero-day attacks makes it a bit more complex.
Traditional antiviruses aren’t that effective in detecting these threats as they are mostly signature-based.
Accordingly, it’s in your best interest to choose a next-generation antivirus that deploys artificial intelligence, machine learning, and other advanced features to keep you as safe as possible.
Above all, practice safe browsing habits to try and steer clear of unknown threats lurking on the internet.
Don’t download unverified software from random websites, and keep a backup of your important data in case of an attack.